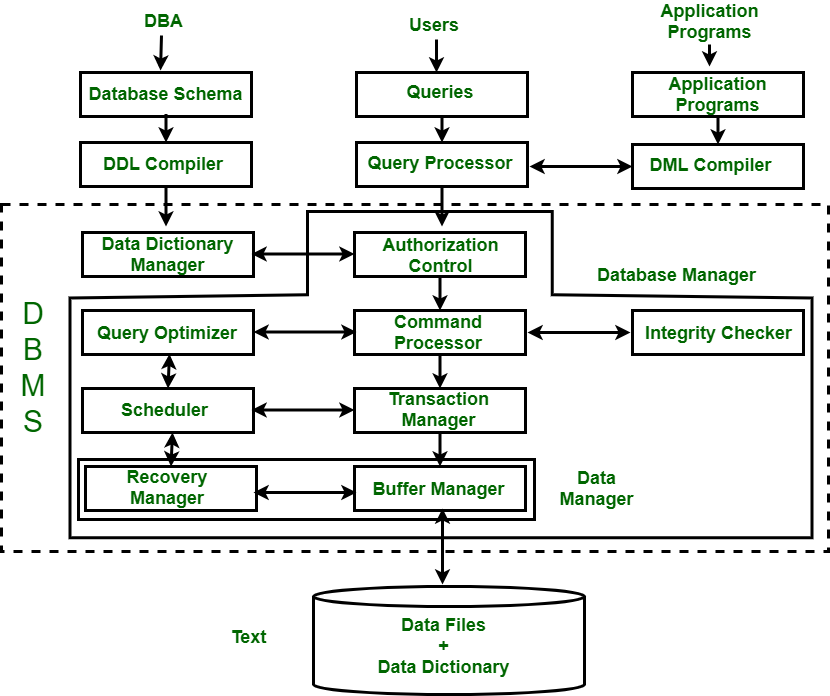
What is Meta Data?
Metadata is data about the data or documentation about the information which is required by the users. In data warehousing, metadata is one of the essential aspects.
Metadata includes the following:
- The location and descriptions of warehouse systems and components.
- Names, definitions, structures, and content of data-warehouse and end-users views.
- Identification of authoritative data sources.
- Integration and transformation rules used to populate data.
- Integration and transformation rules used to deliver information to end-user analytical tools.
- Subscription information for information delivery to analysis subscribers.
- Metrics used to analyze warehouses usage and performance.
- Security authorizations, access control list, etc.
Metadata is used for building, maintaining, managing, and using the data warehouses. Metadata allow users access to help understand the content and find data.
everal examples of metadata are:
- A library catalog may be considered metadata. The directory metadata consists of several predefined components representing specific attributes of a resource, and each item can have one or more values. These components could be the name of the author, the name of the document, the publisher's name, the publication date, and the methods to which it belongs.
- The table of content and the index in a book may be treated metadata for the book.
- Suppose we say that a data item about a person is 80. This must be defined by noting that it is the person's weight and the unit is kilograms. Therefore, (weight, kilograms) is the metadata about the data is 80.
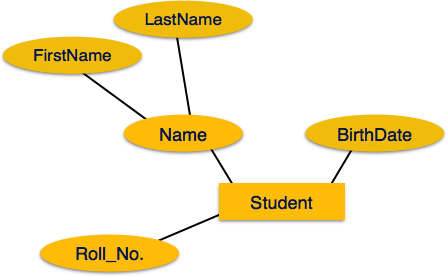
- Another examples of metadata are data about the tables and figures in a report like this book. A table (which is a record) has a name (e.g., table titles), and there are column names of the tables that may be treated metadata. The figures also have titles or names.